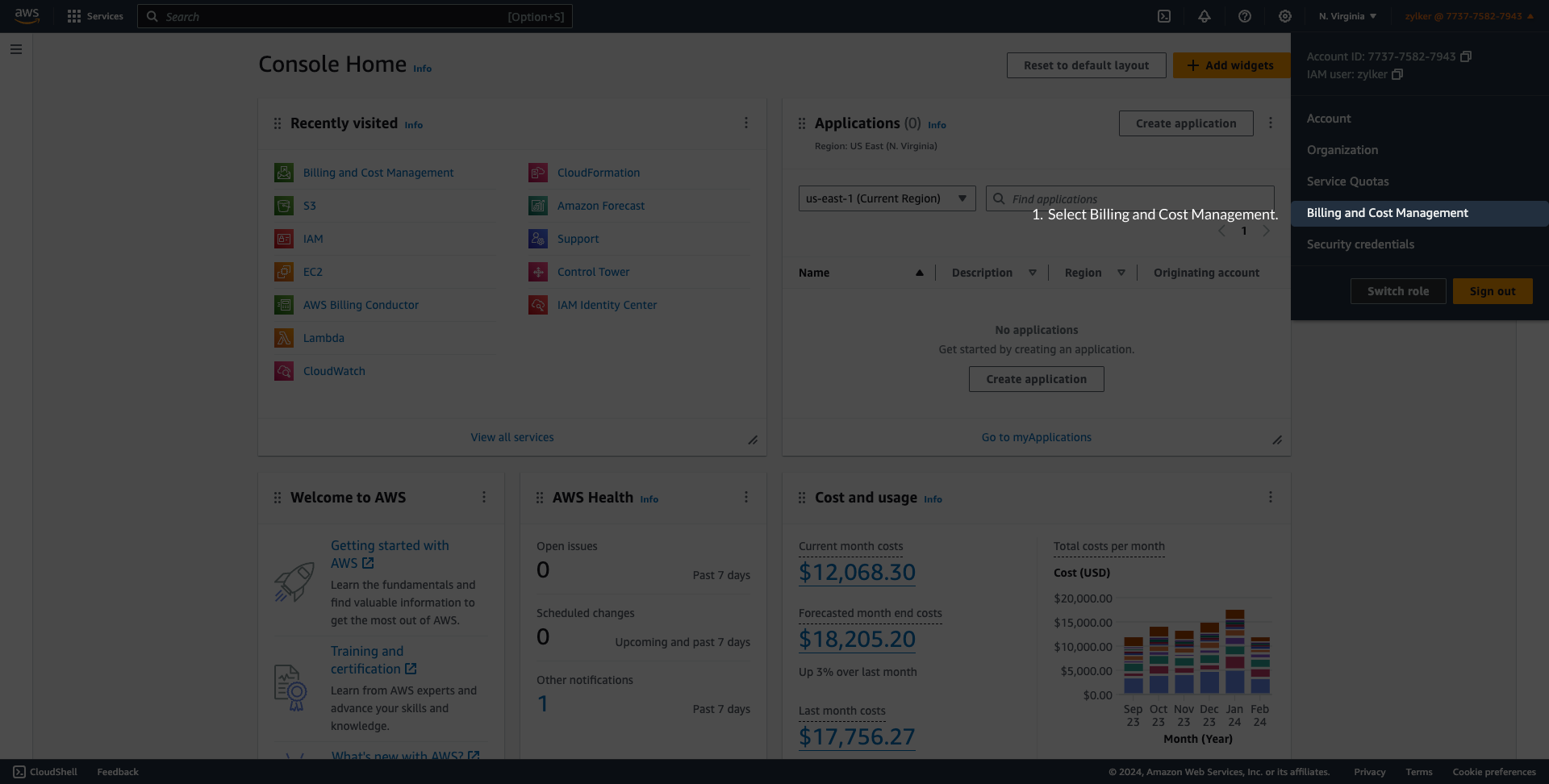
Integrate Amazon Web Services Account with CloudSpendIntegrating your AWS account with CloudSpend provides a comprehensive view of your cloud spending. Connecting an AWS account with CloudSpendConnecting your AWS account with CloudSpend is a three stage process:
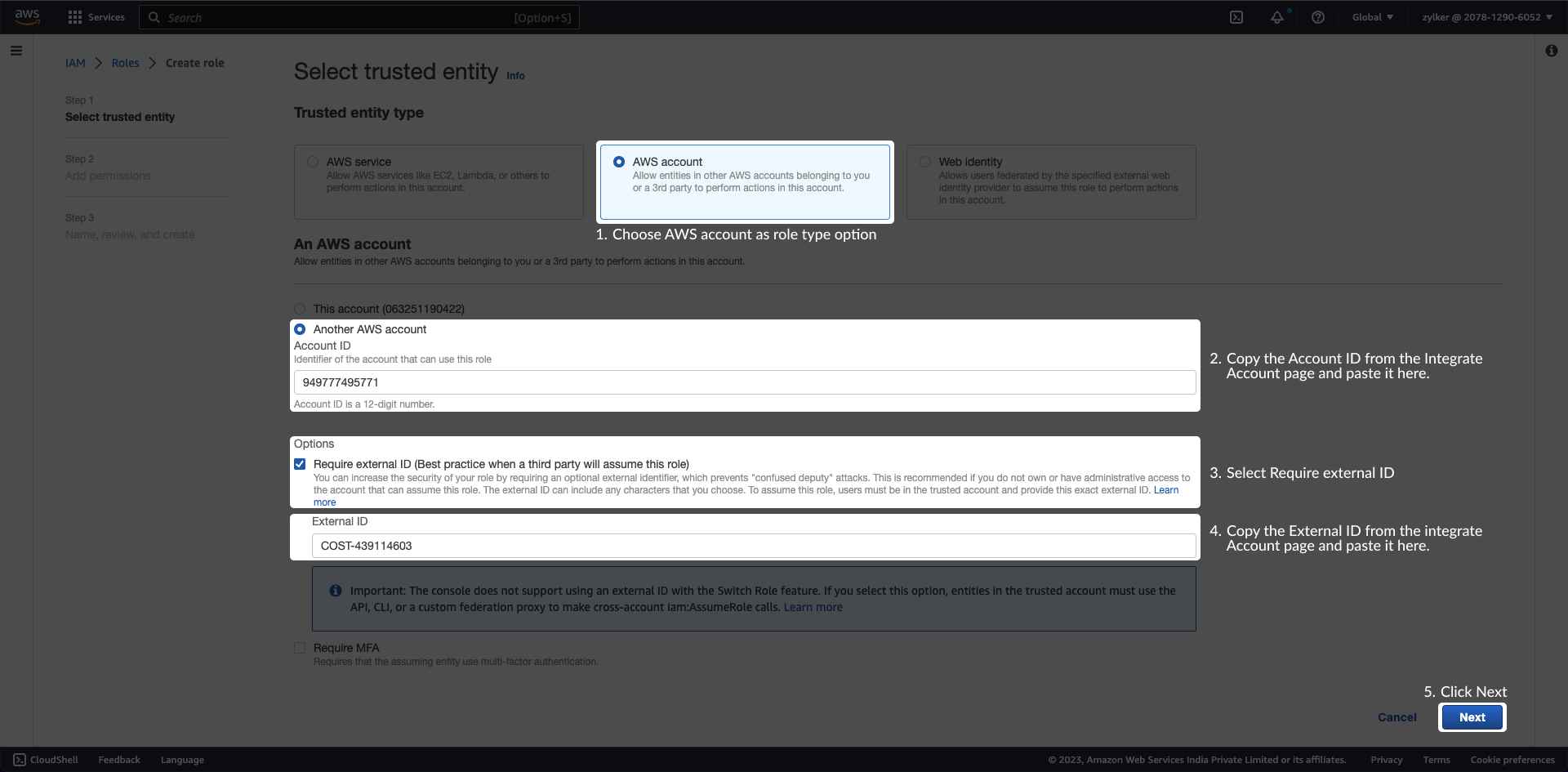
Enable programmatic access (Stage 1)You can provide CloudSpend programmatic access to your AWS resources using two ways. You can create a cross-account IAM Role and establish a trust relationship between your AWS account and CloudSpend's AWS account. Between the two, IAM Role is recommended as there is no sharing of security credentials. Also when you delegate permissions using Roles, you can designate the AWS accounts that are allowed to assume the role, thereby safeguarding your account from unauthorized access. We're deprecating IAM user based access to new users. So if you're existing users, you can switch to IAM role based access. IAM role based accessThe following section will walk you through the IAM Role creation process: Get your External ID
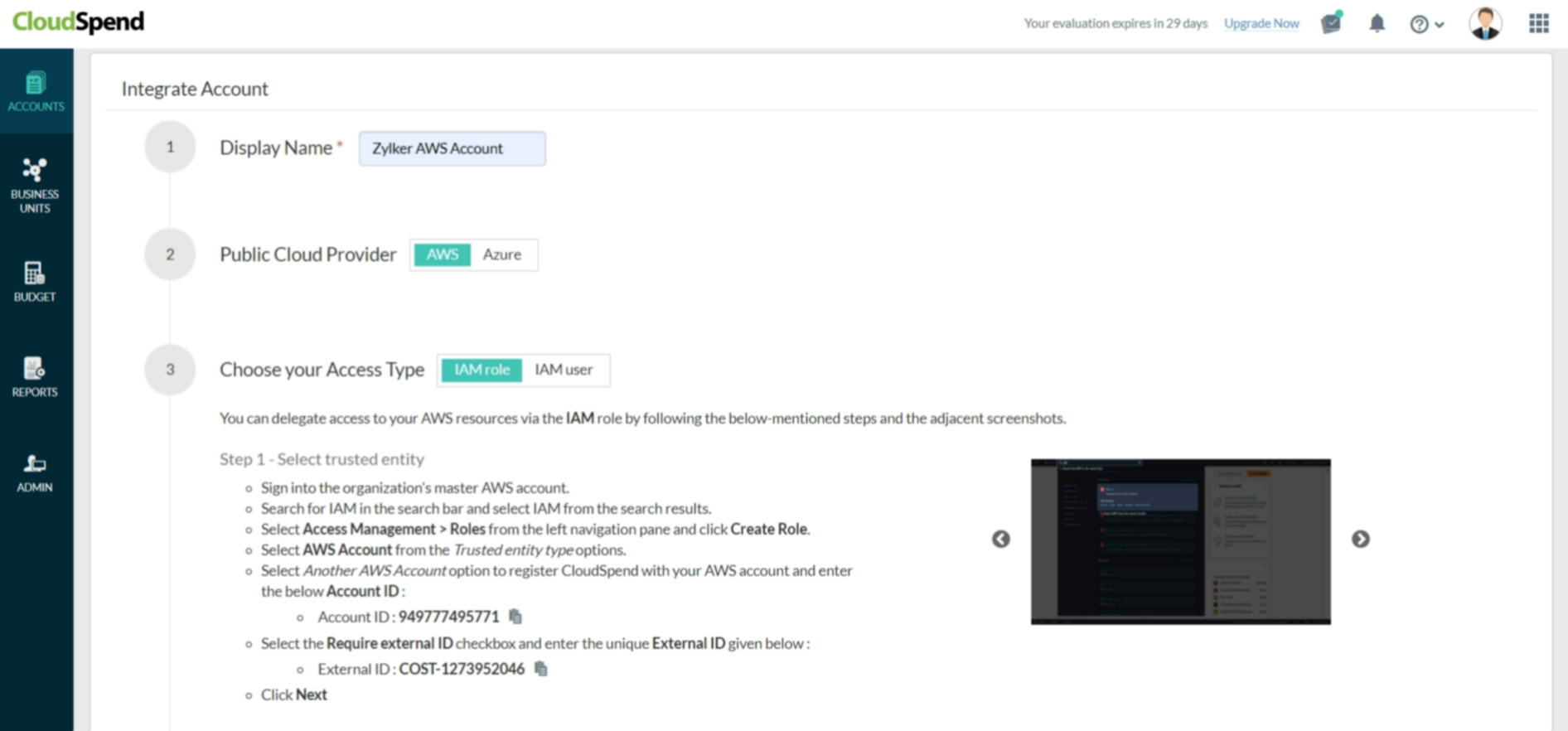
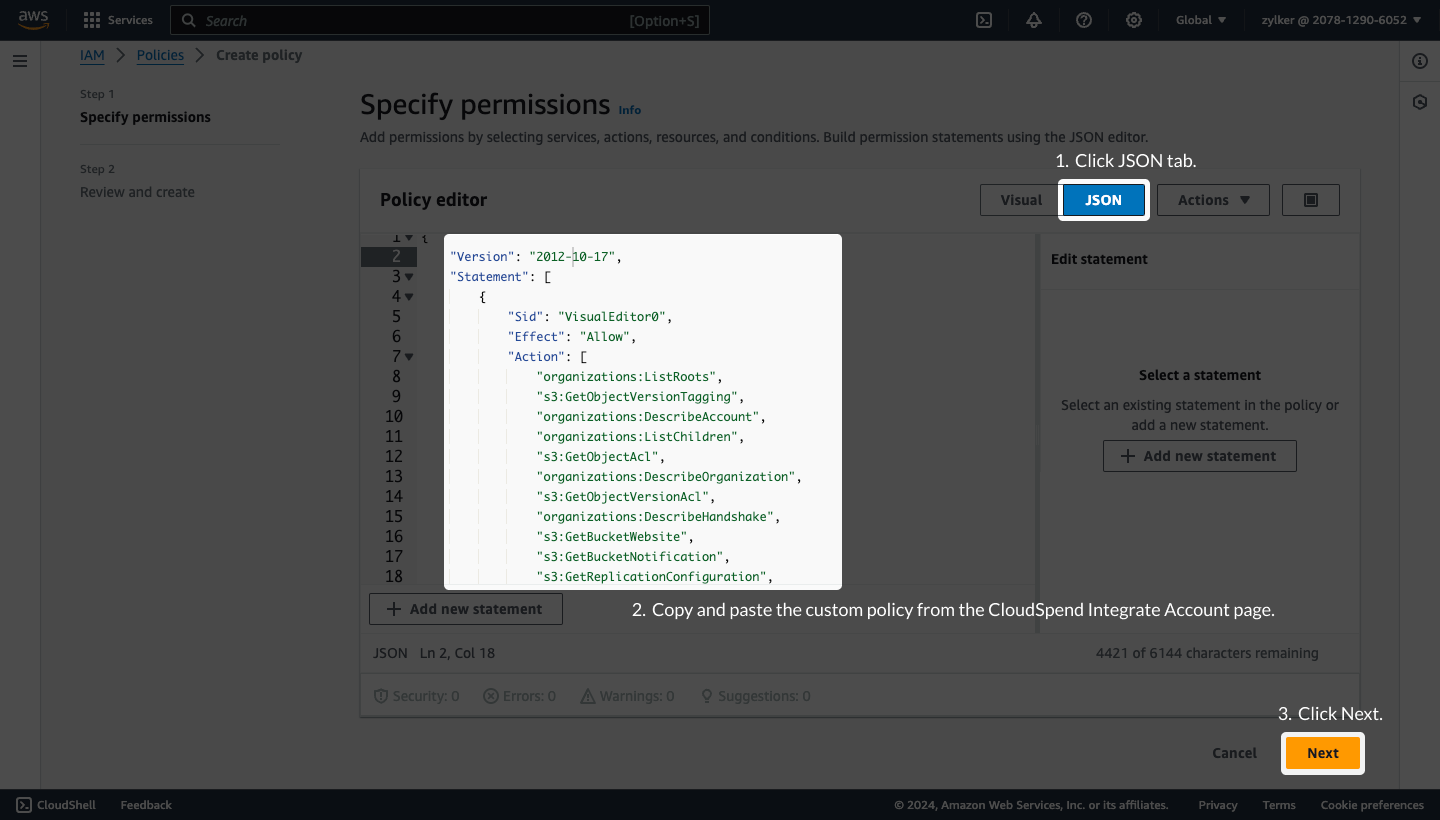
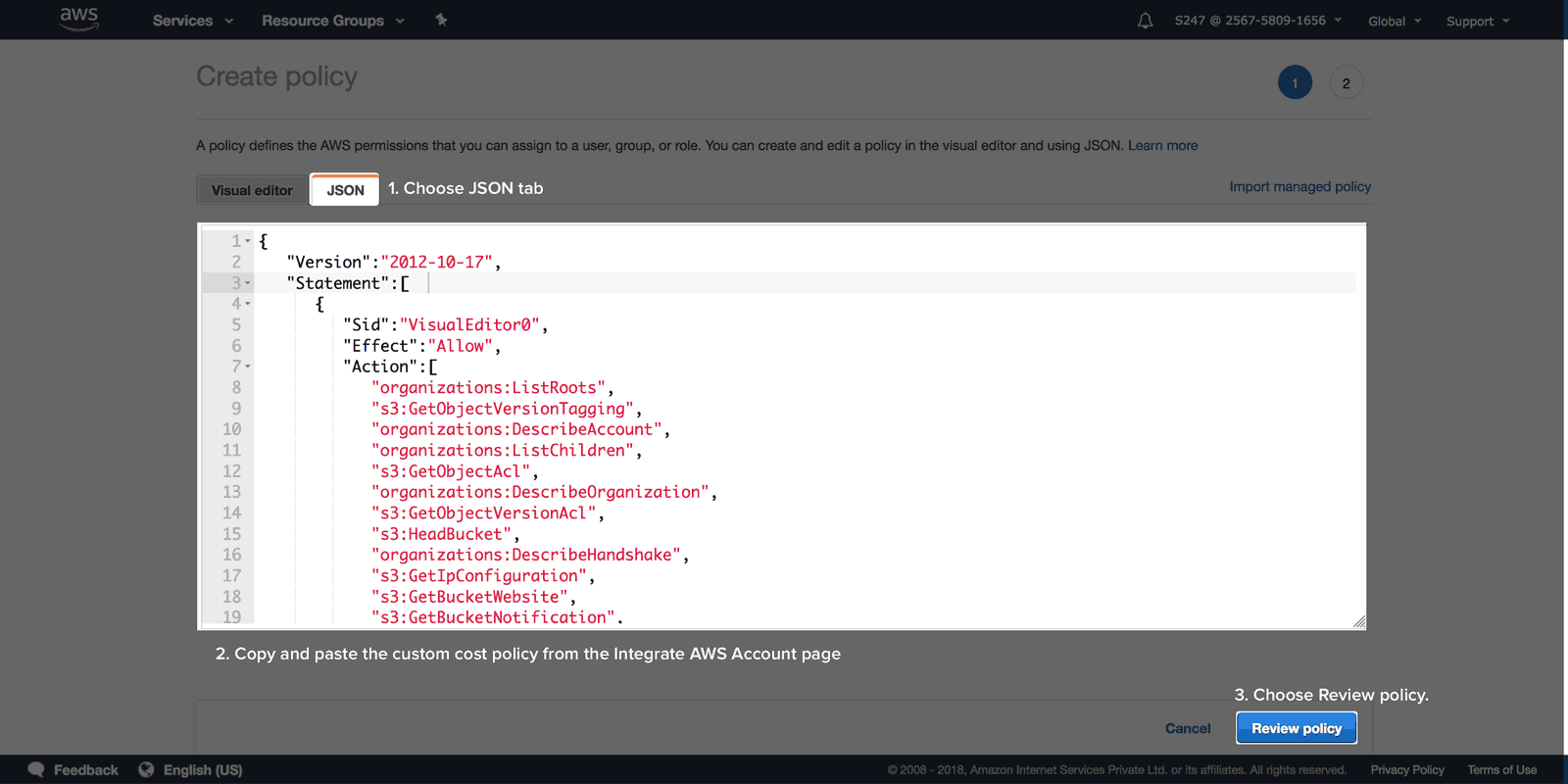
The External ID is an alpha-numeric key unique to your account. The key gets regenerated every time you refresh the Integrate AWS Account page. So, please make sure you use the correct key during IAM Role creation. Ensure that you have the required policies for CloudSpend. If not, create your own policy before you create an IAM role. To do so, follow the steps mentioned below:
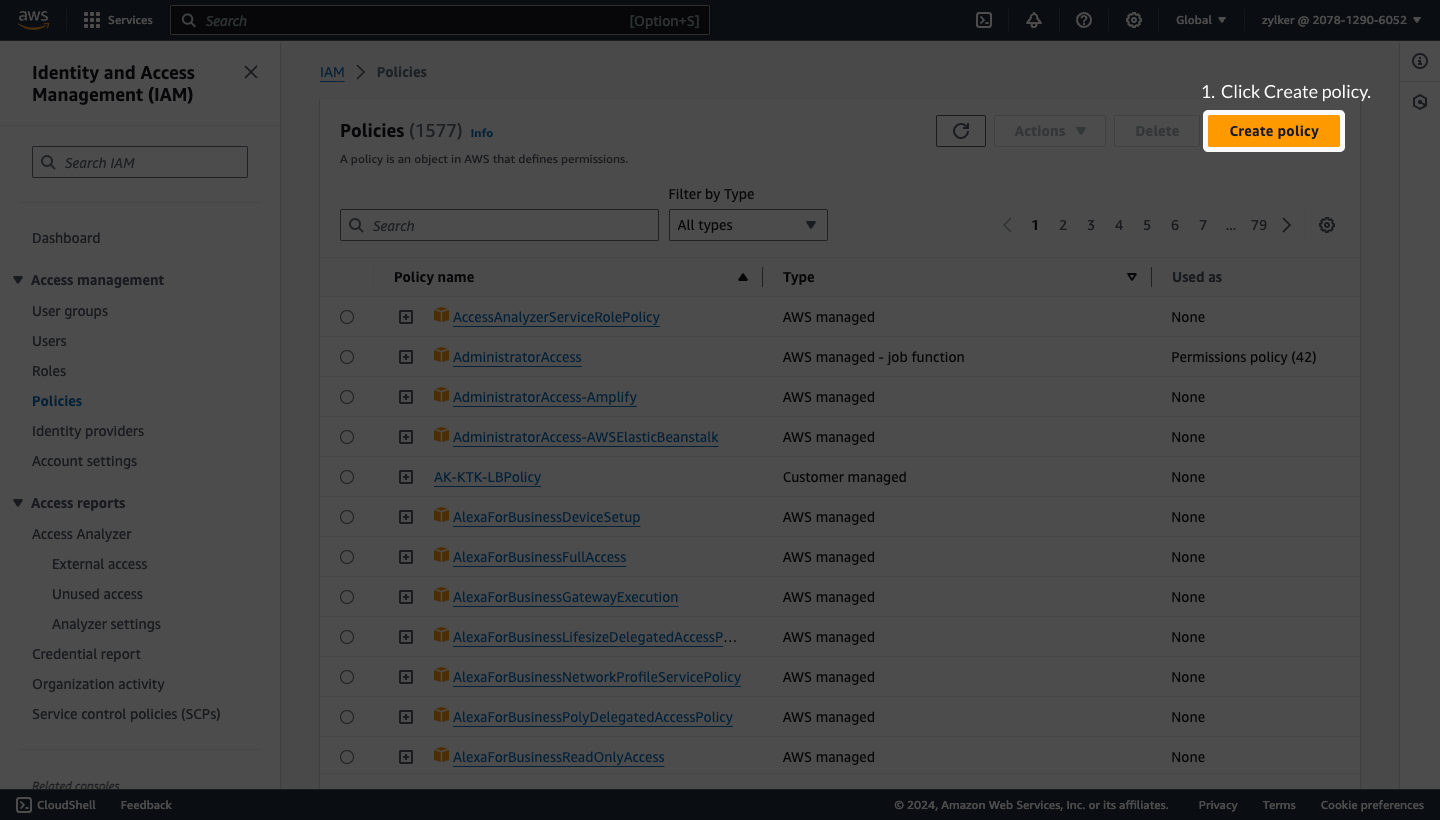
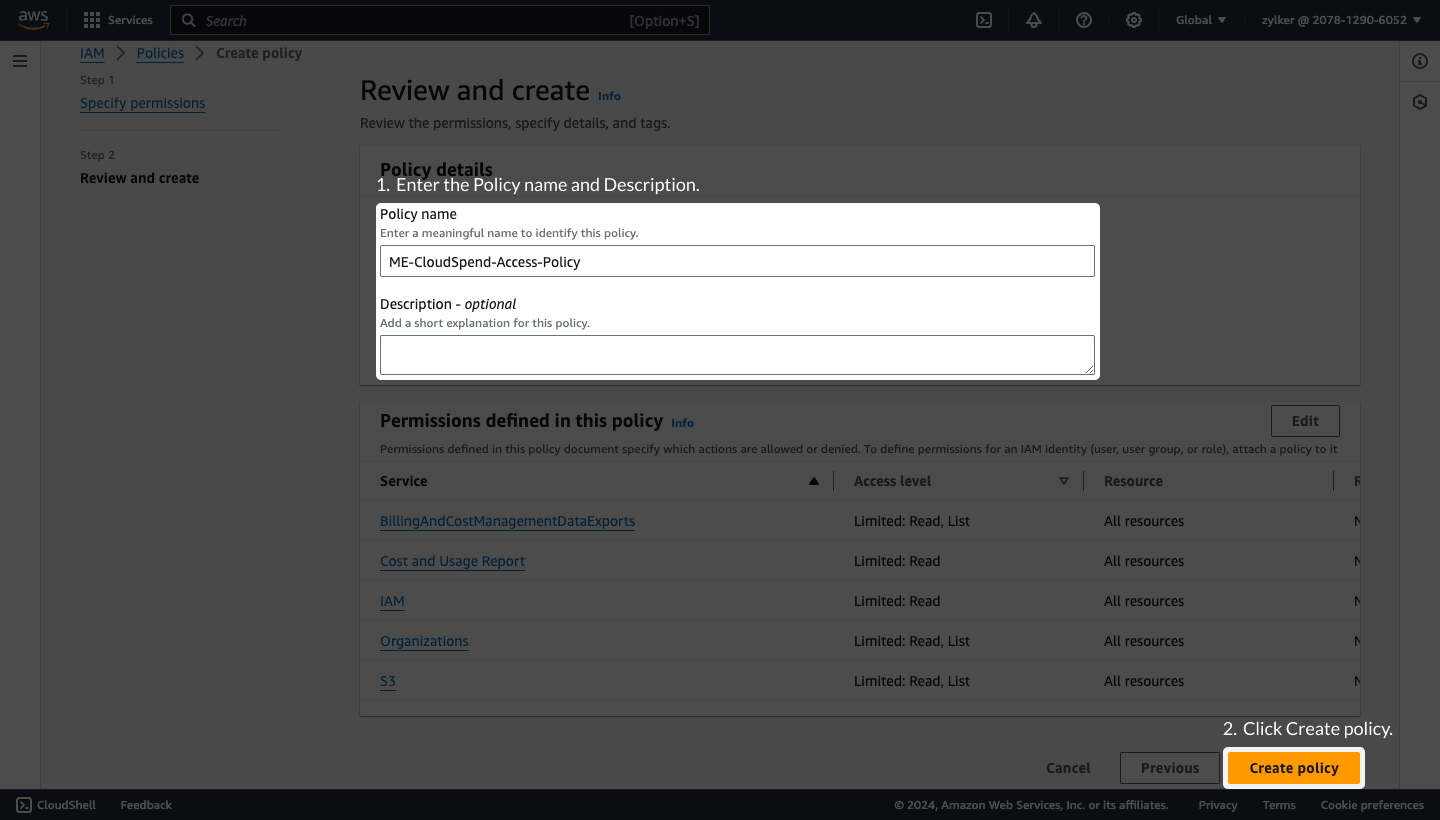
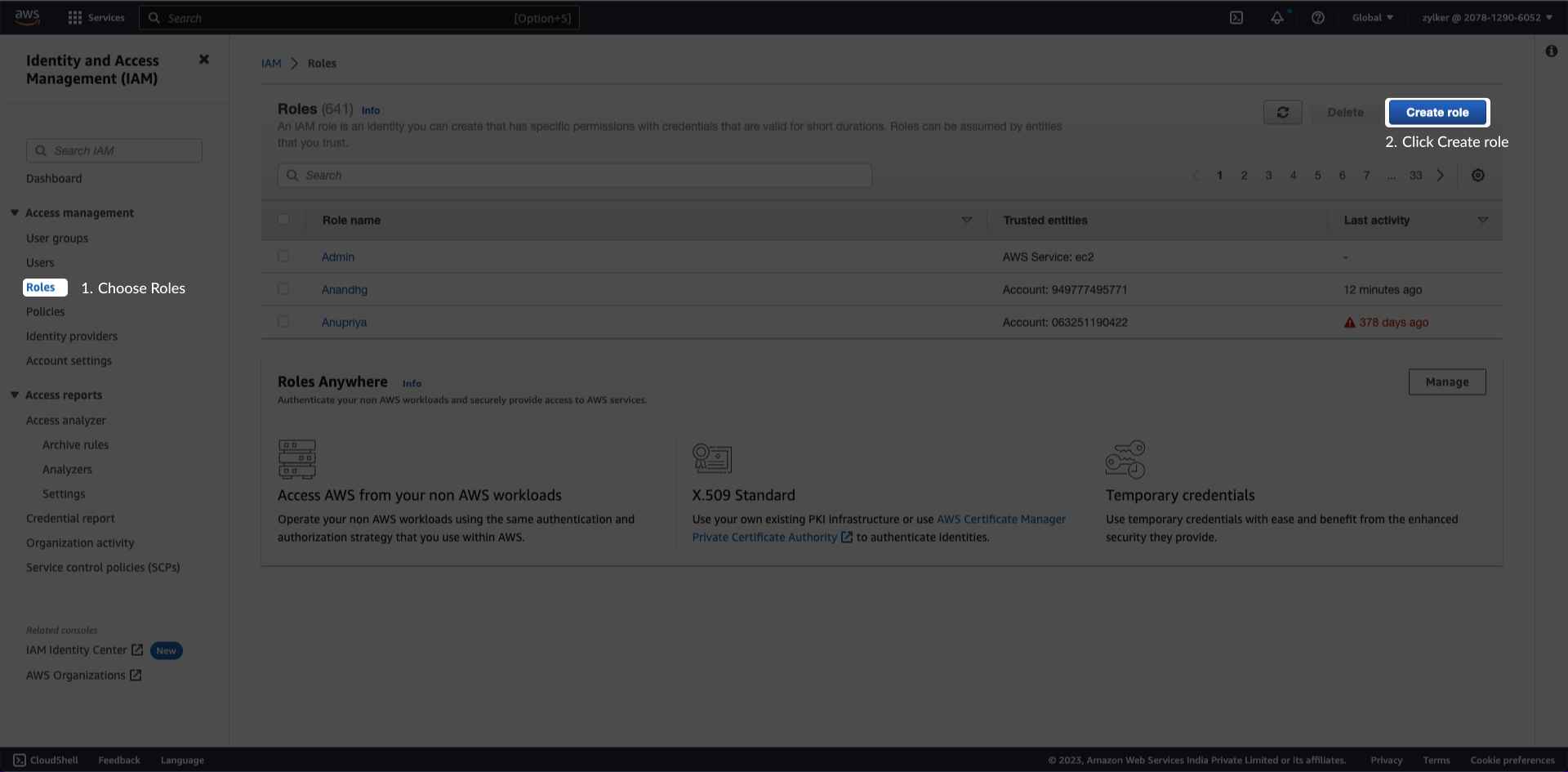
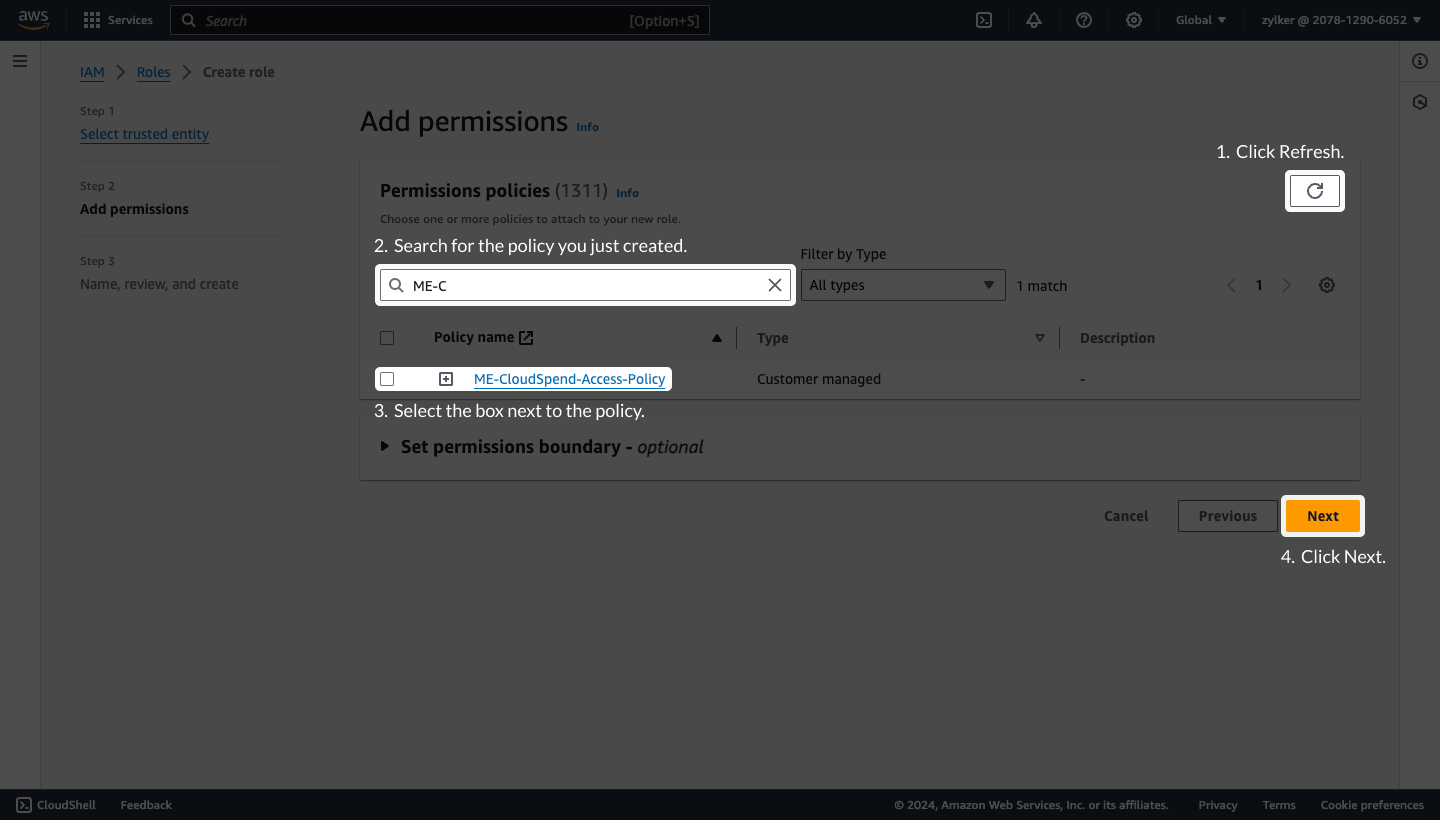
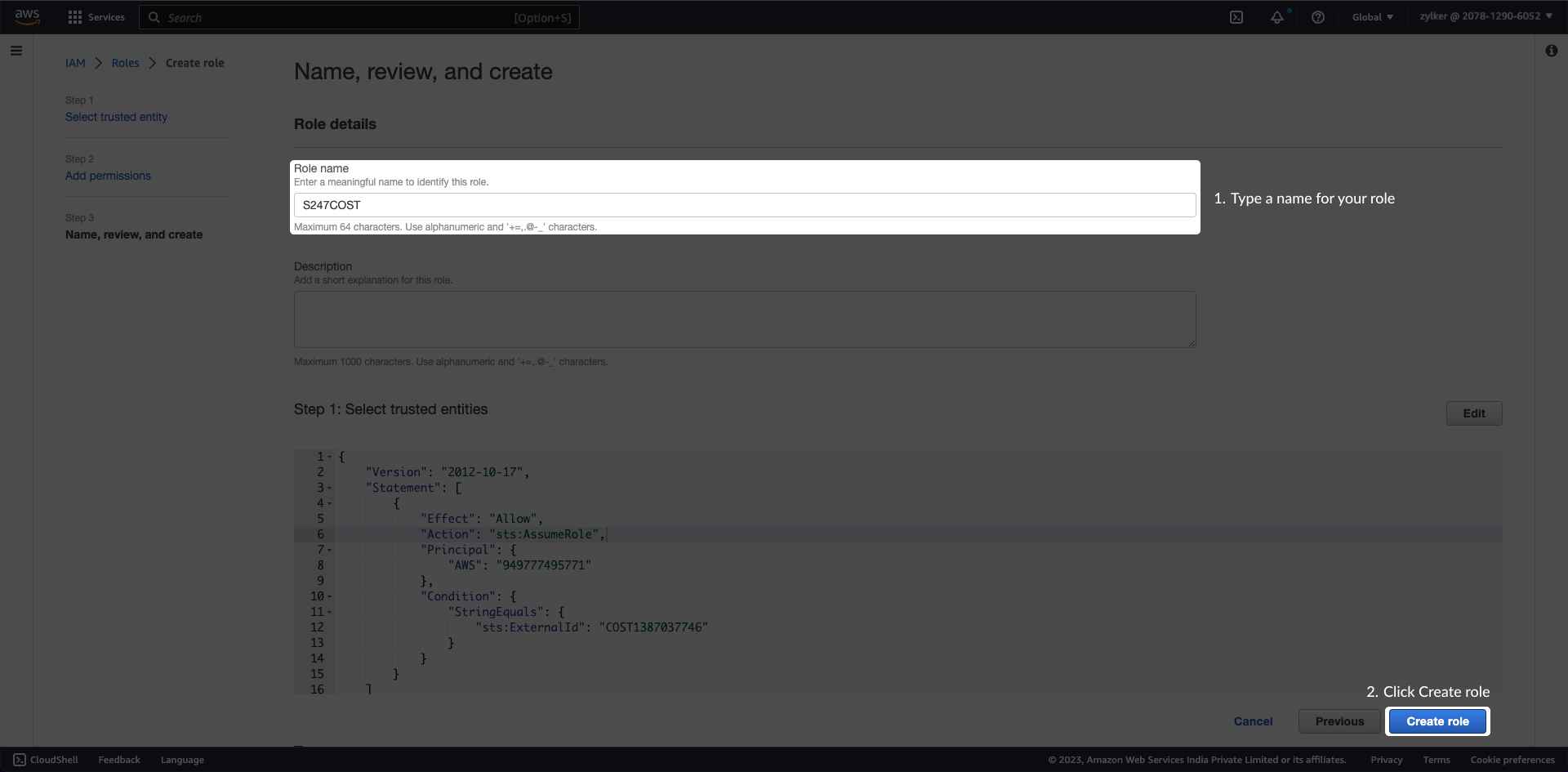
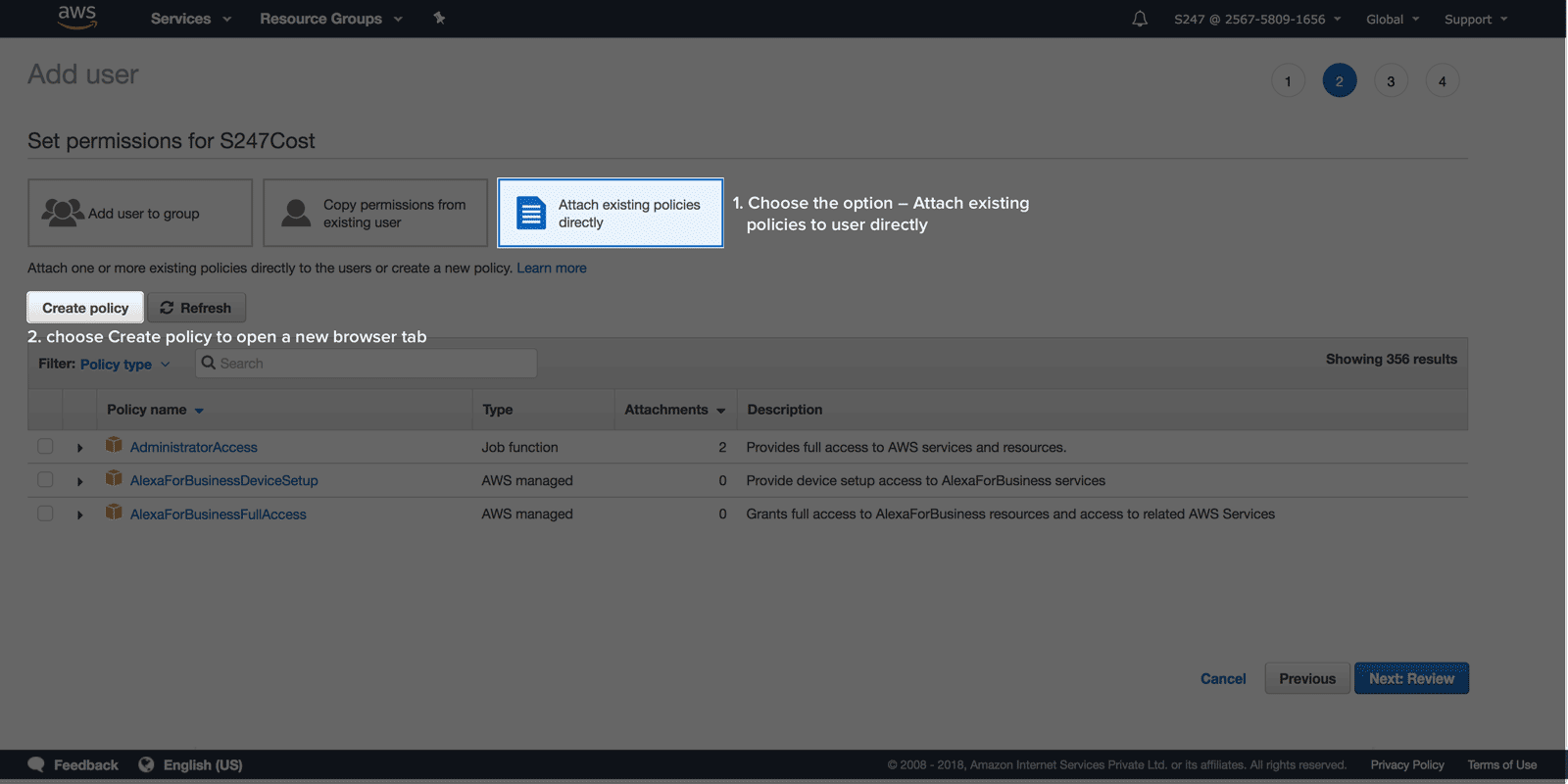
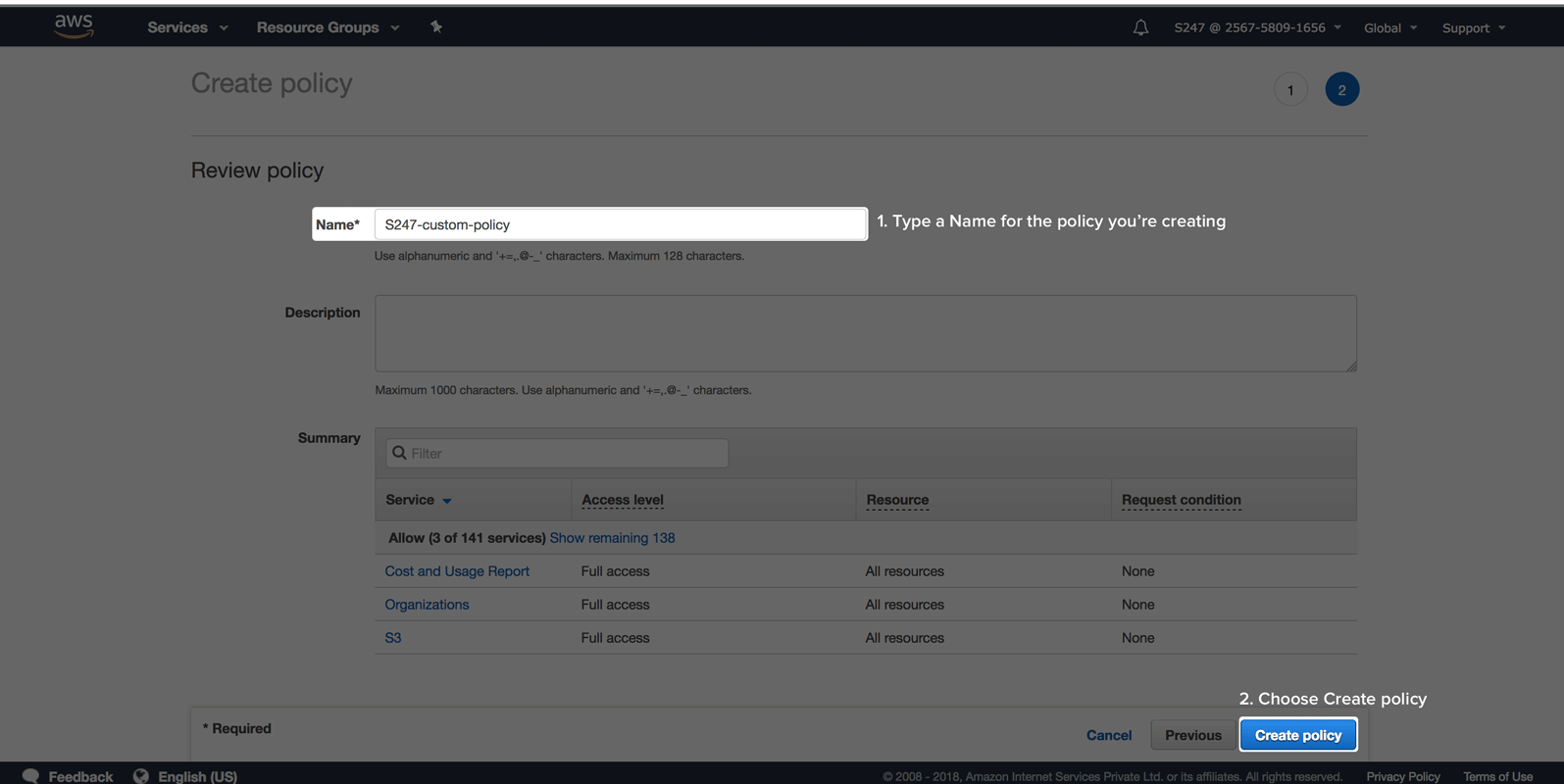
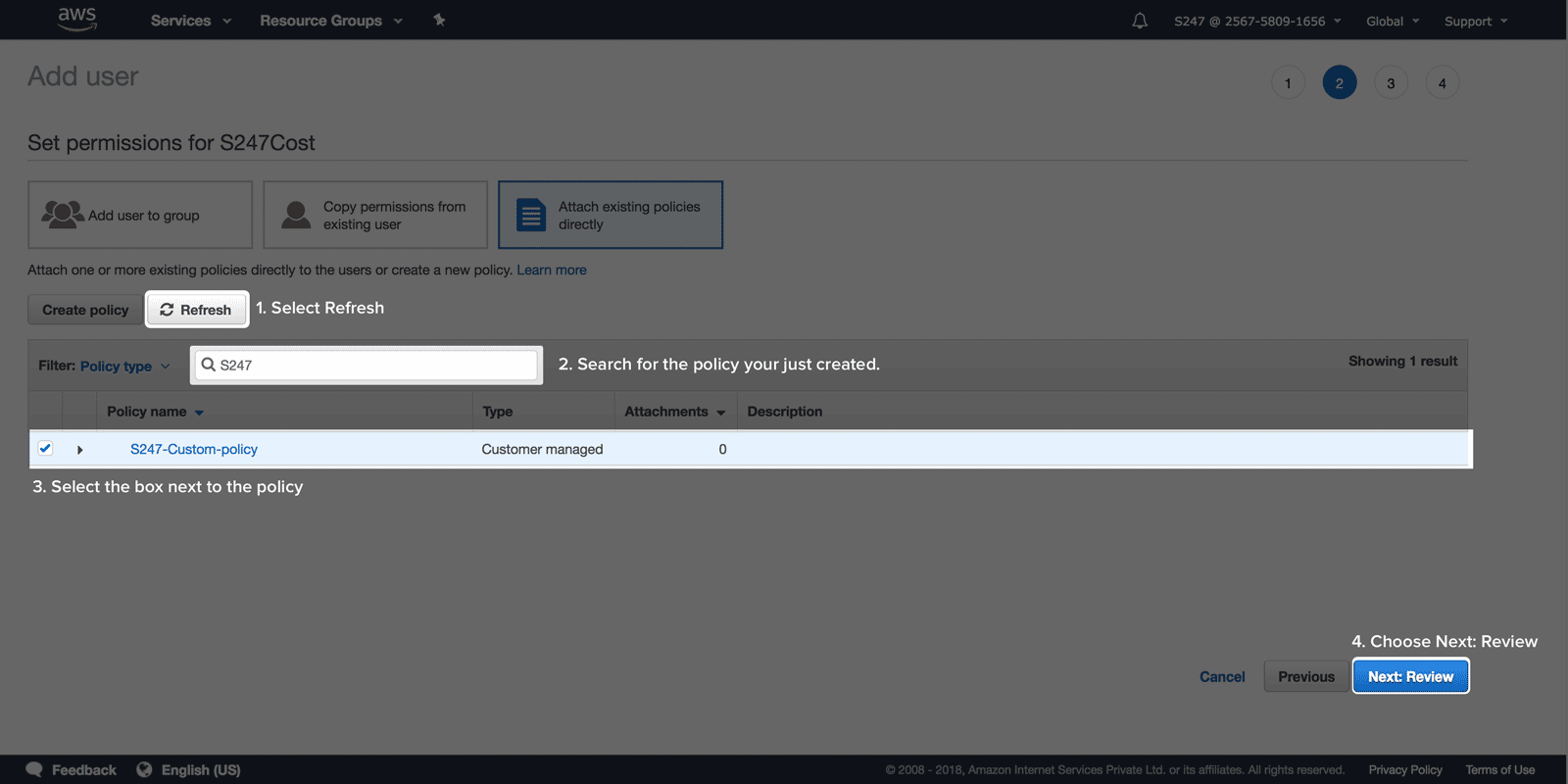
Create an IAM roleTo create an IAM role follow the below mentioned steps:
Site24x7 requires ReadOnly access to your AWS services and resources.
Step 3: Name, review, and create
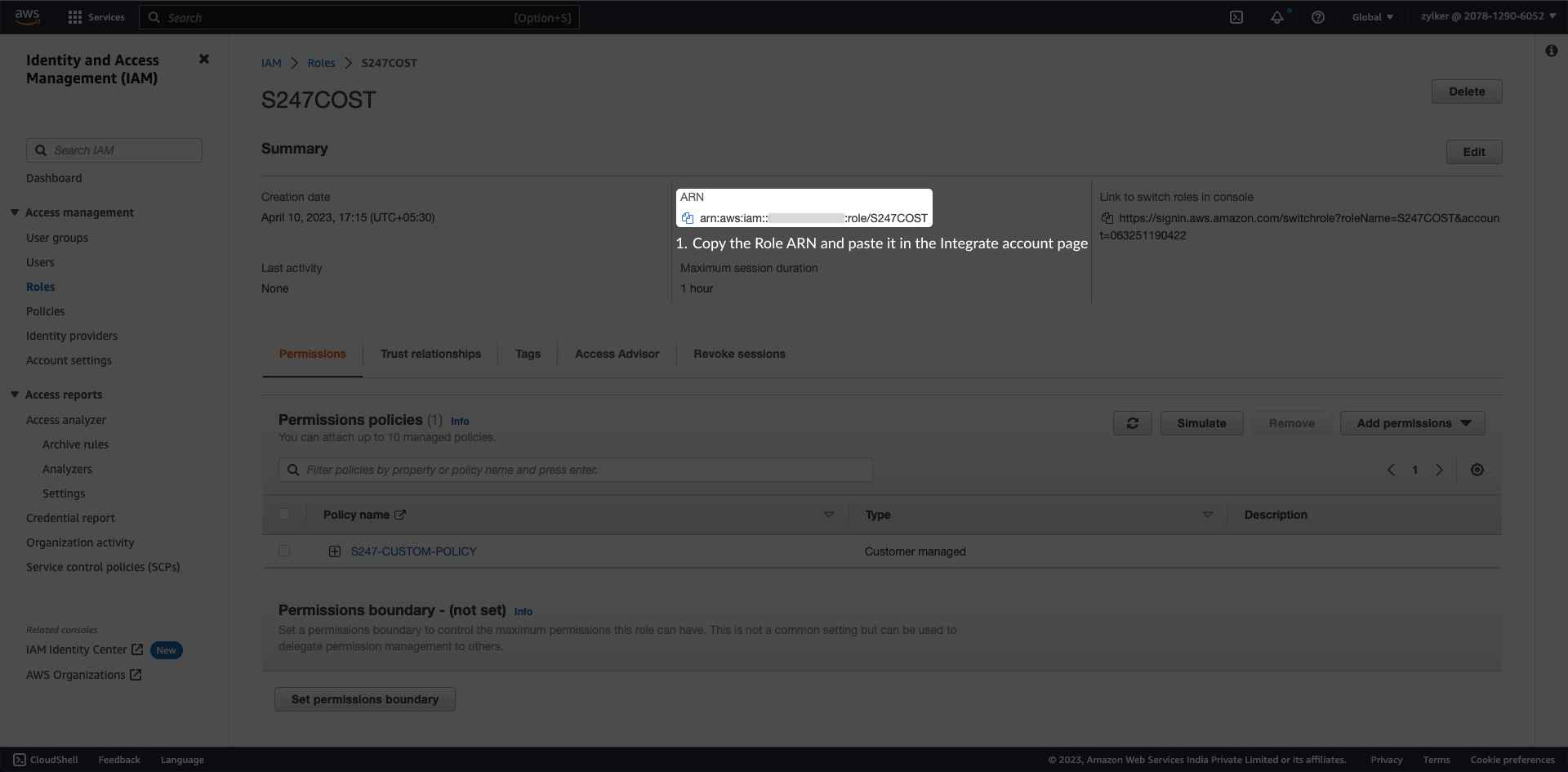
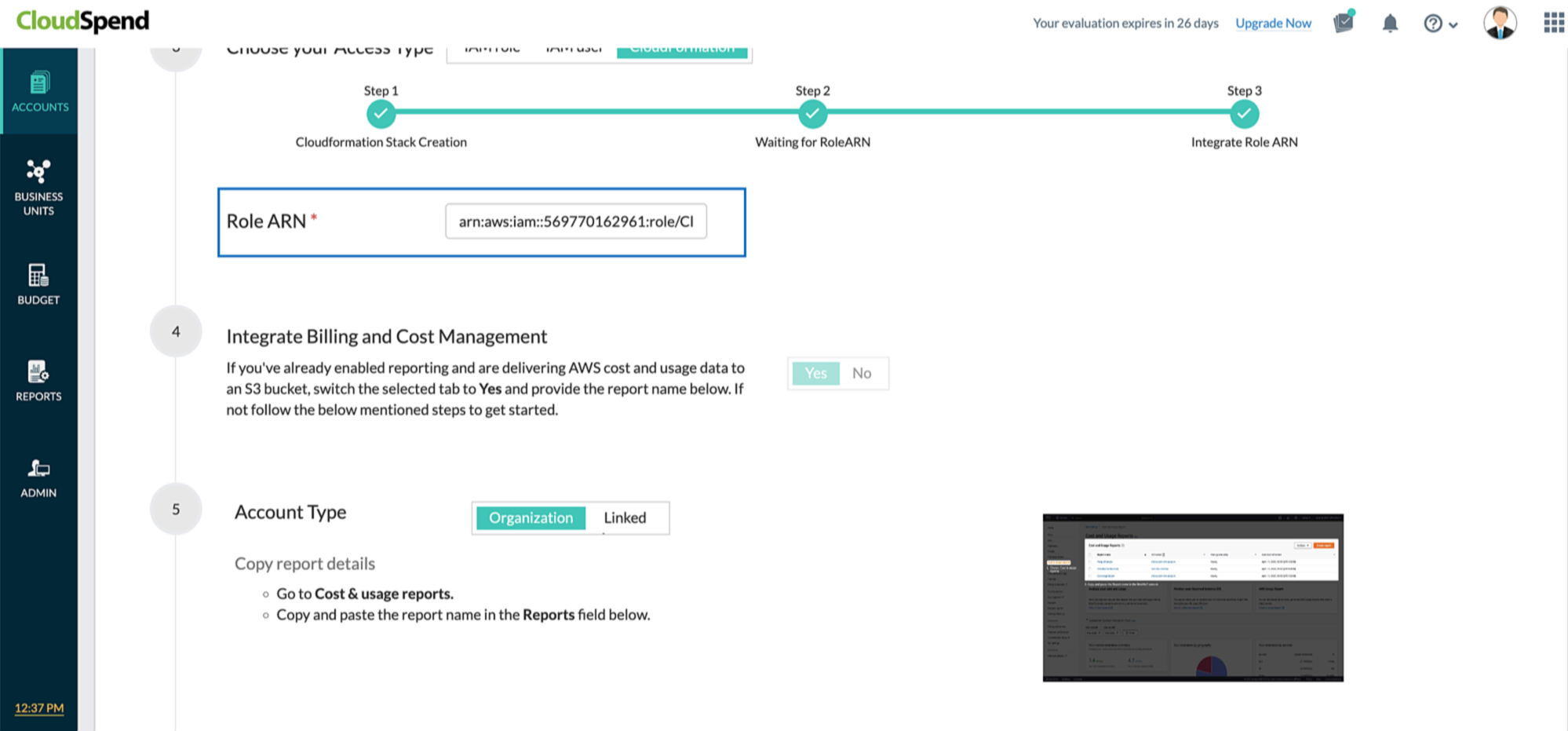
Copy Role ARN
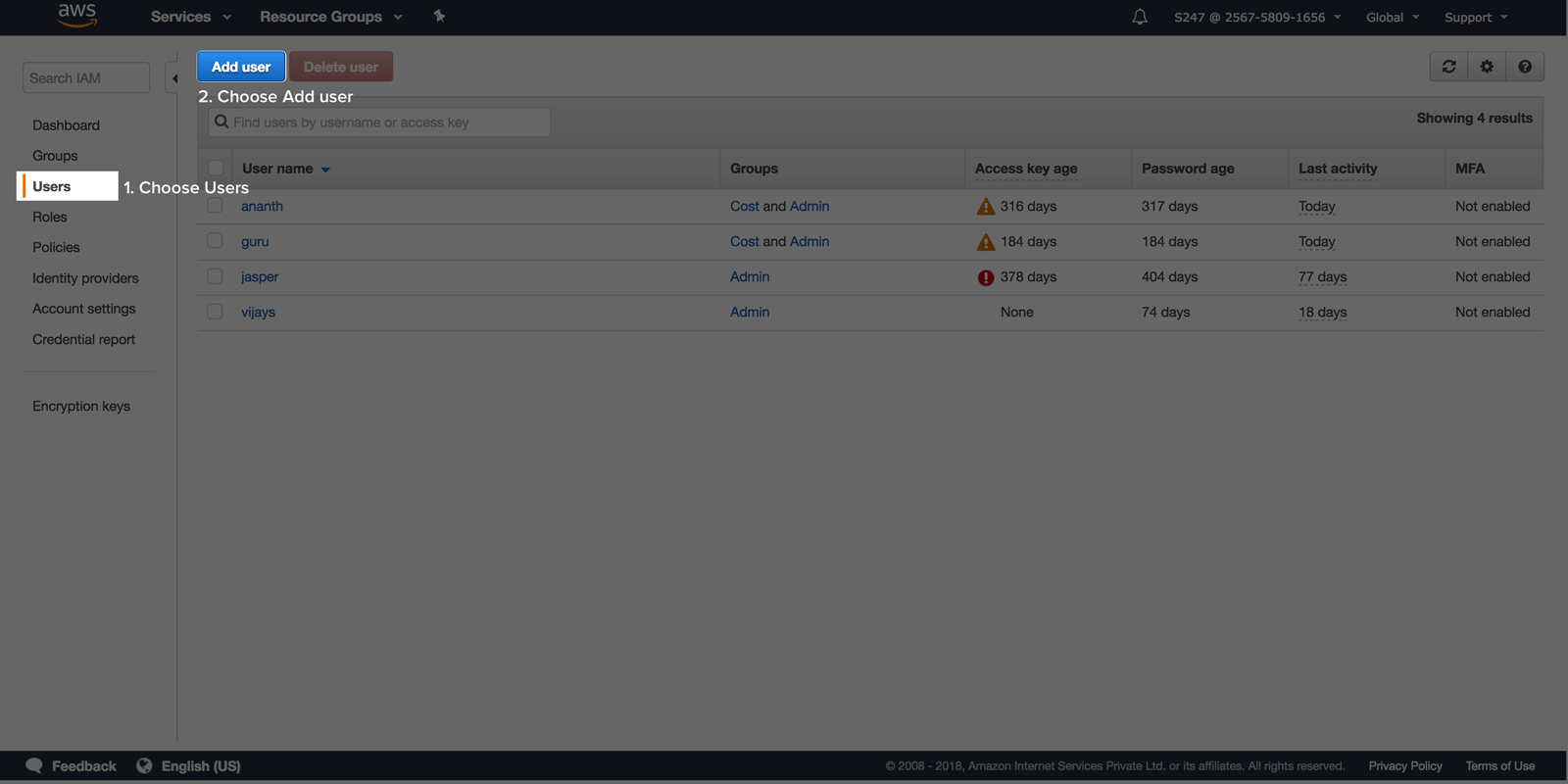
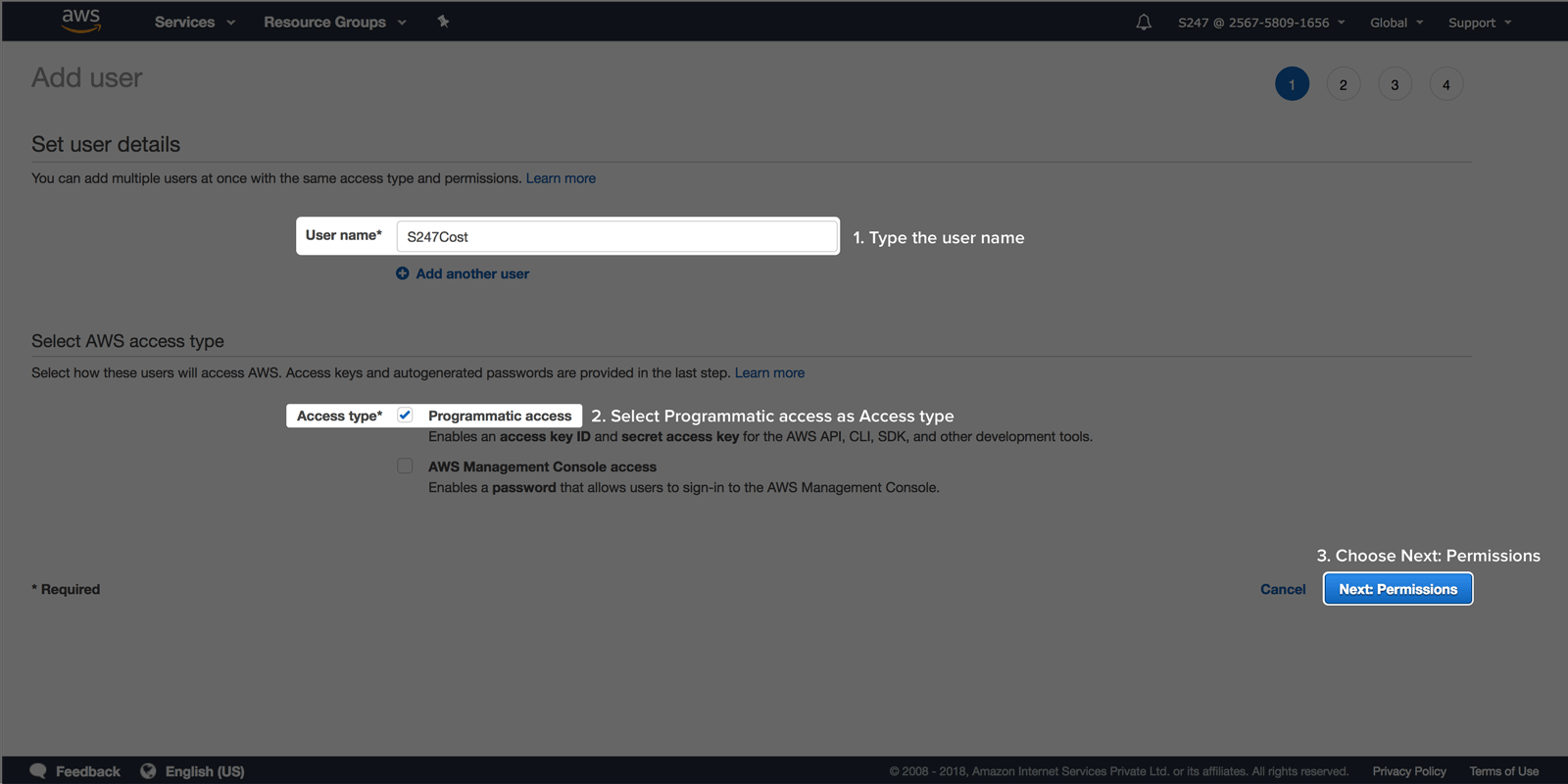
IAM User based access (deprecated)The following section will walk you through the AWS IAM user creation process: Select Access Type
Assign permissions
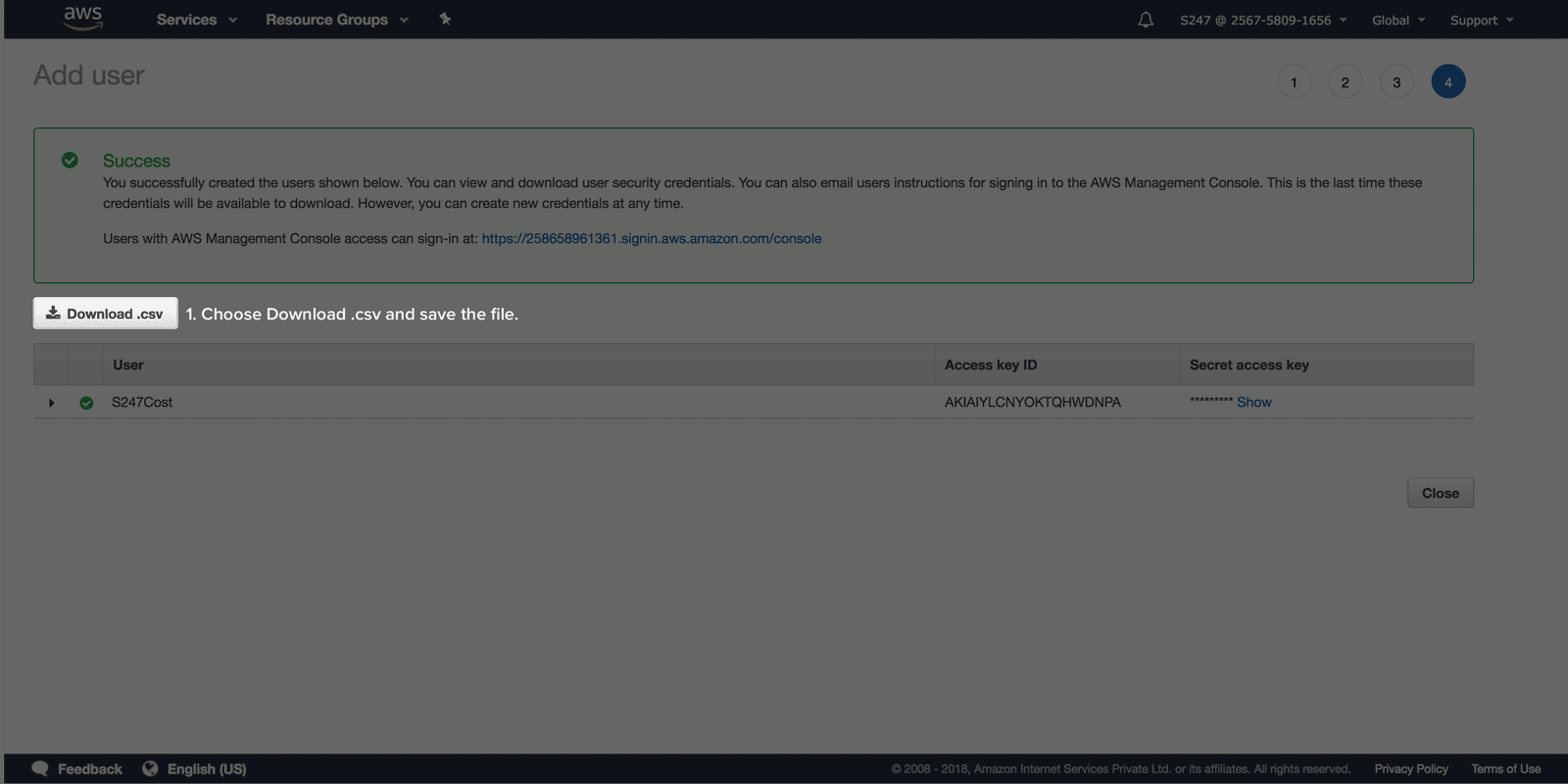
Download credentials
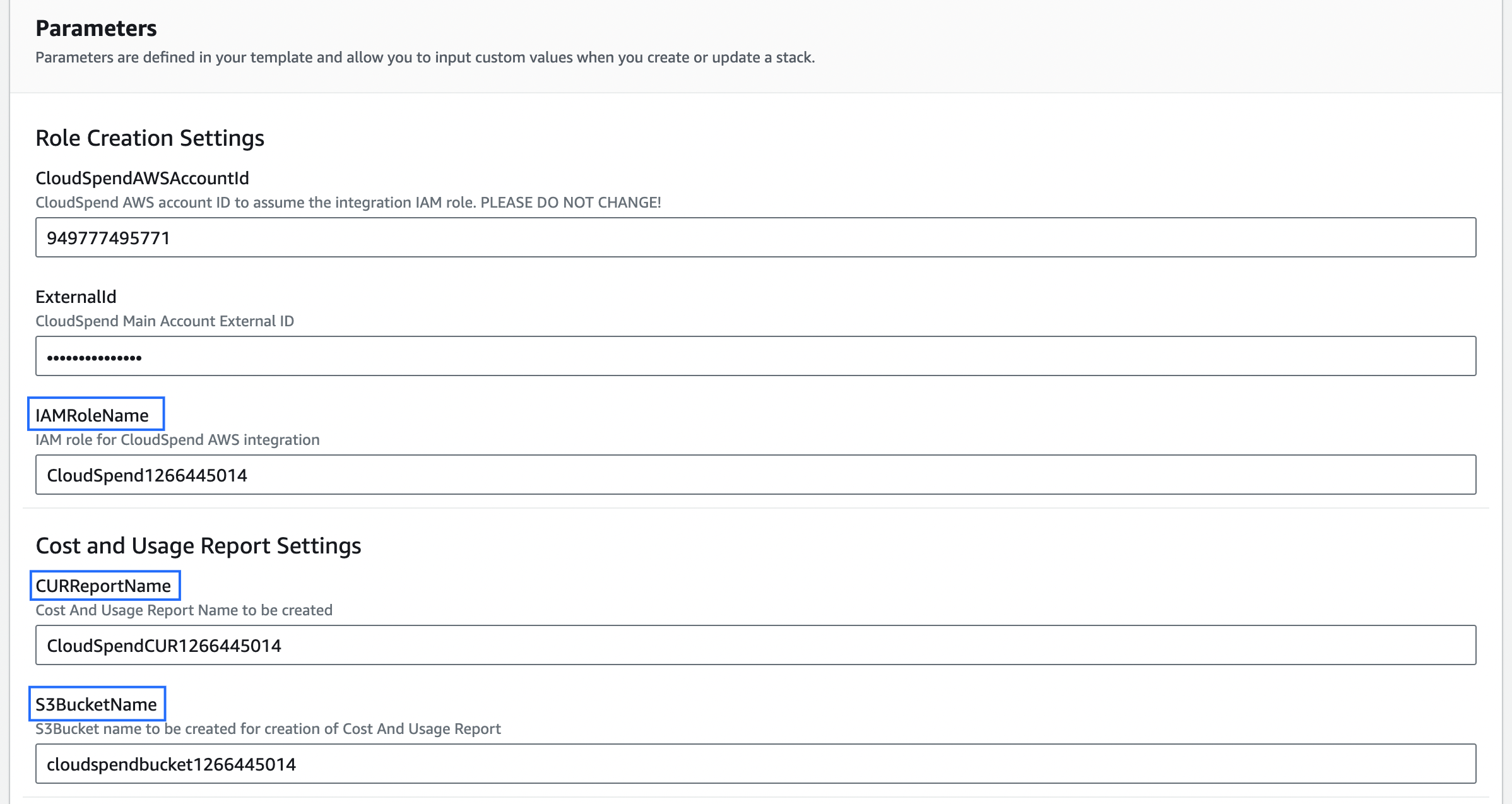
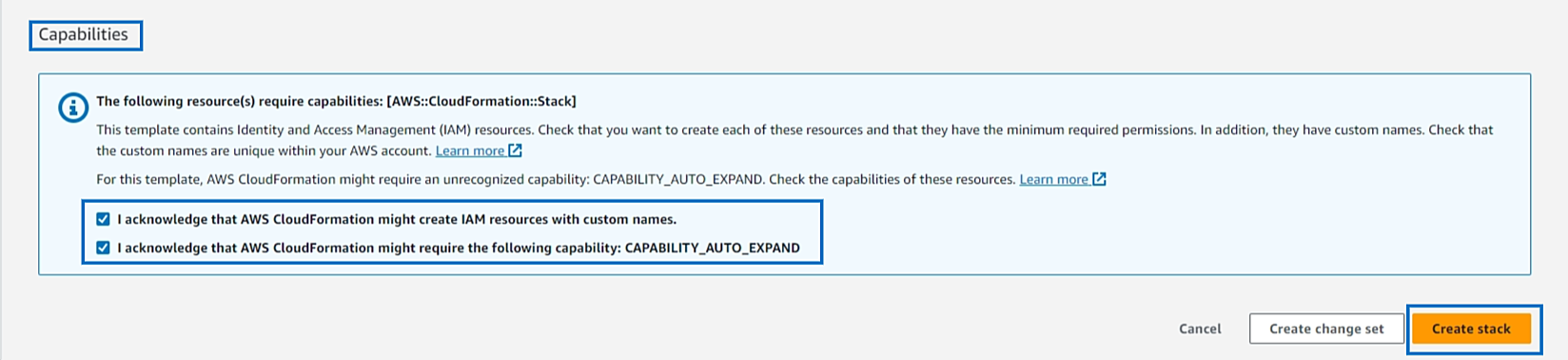
AWS CloudFormation stack based accessCloudSpend uses an AWS CloudFormation template to generate an IAM role, so that you can seamlessly integrate your AWS account with CloudSpend. Enabling access to your AWS environment automatically creates an IAM role using the CloudFormation template. The following section will walk you through the IAM Role creation process using CloudFormation stack:
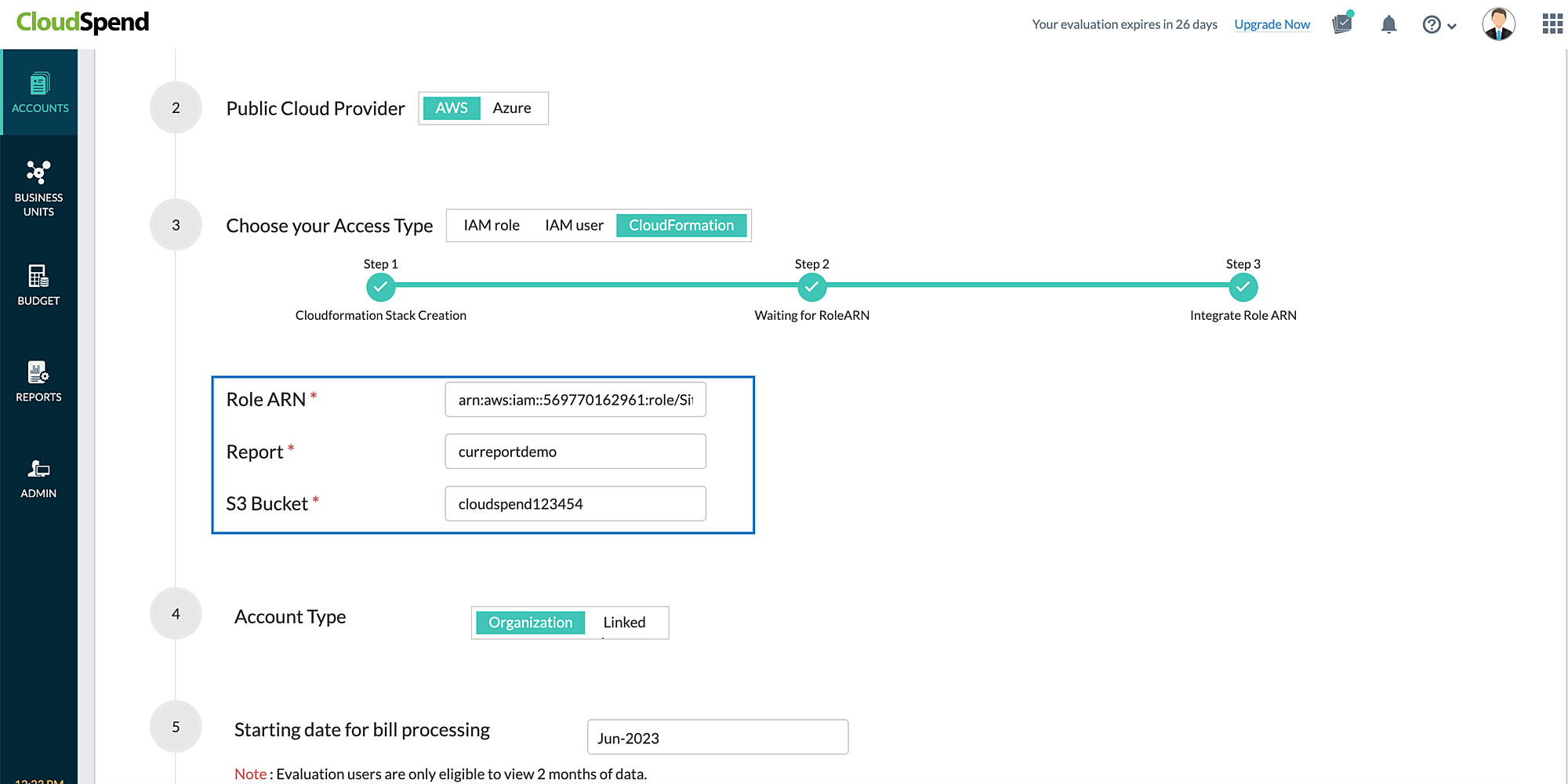
If the Cost and Usage Report creation needed option is set to No then, CloudSpend creates only the role ARN via Lambda function. Once the role ARN details are fetched, the Role ARN field is auto-filled. You will have to enter the report name in the Report field manually.
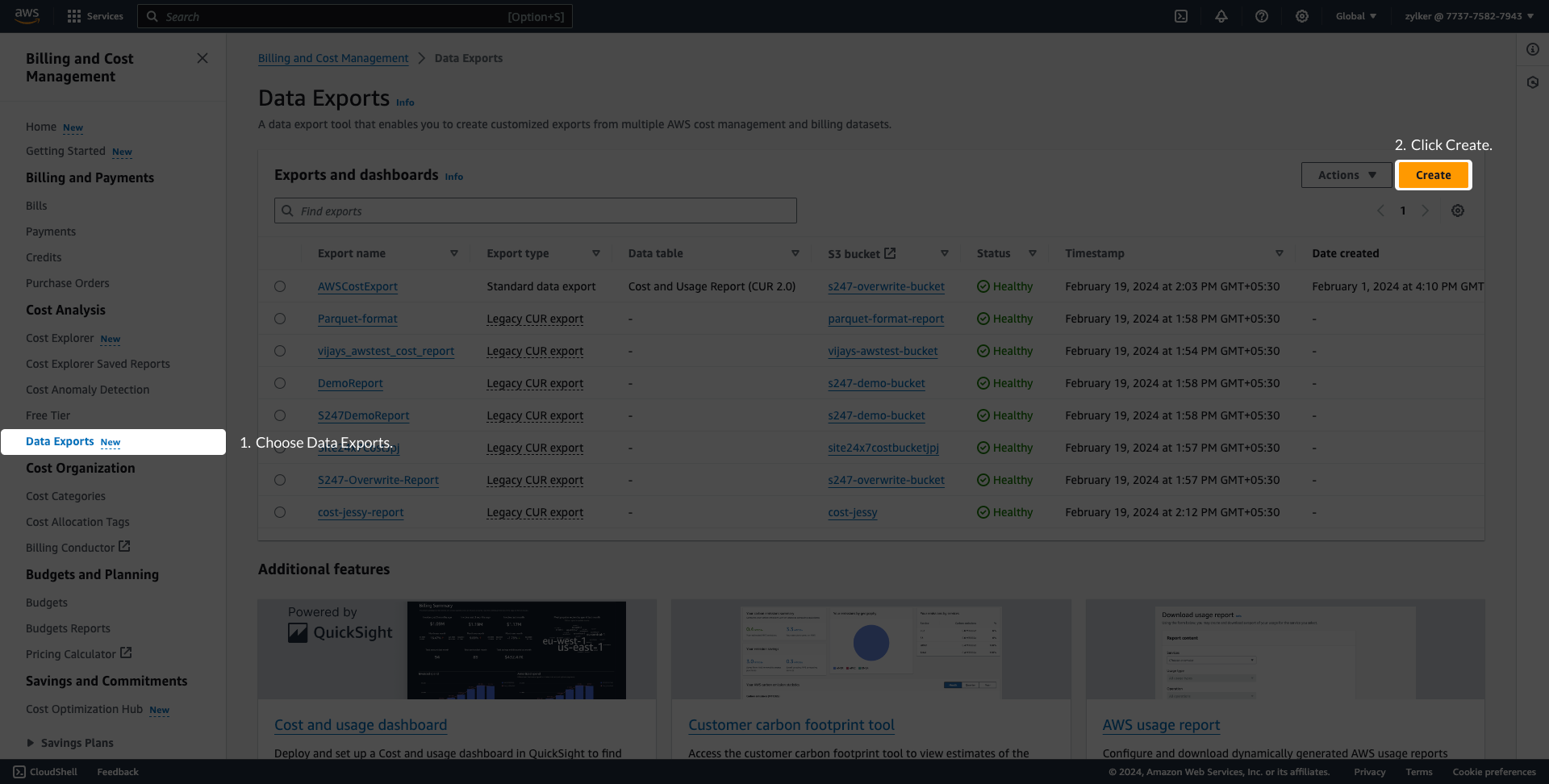
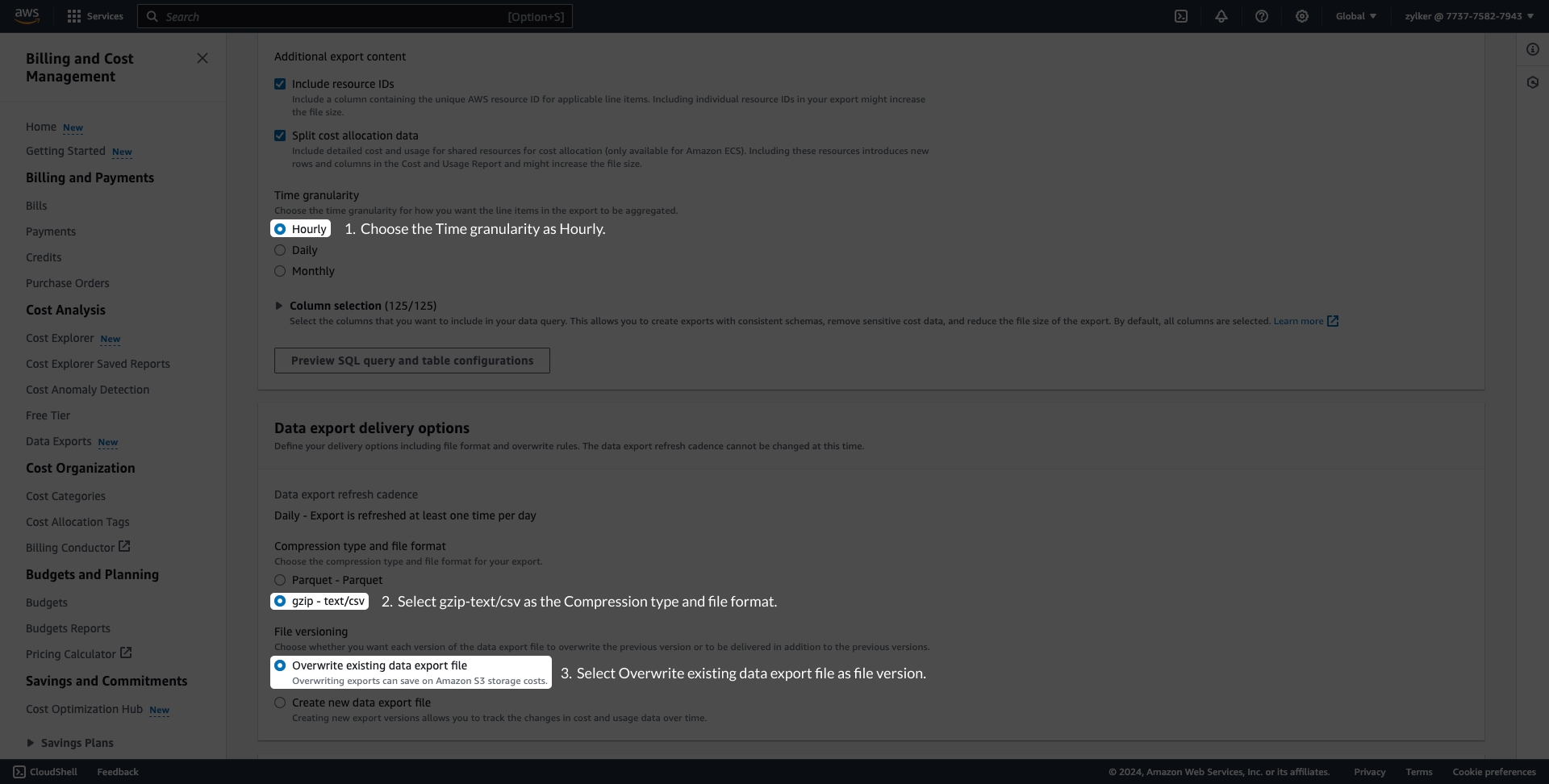
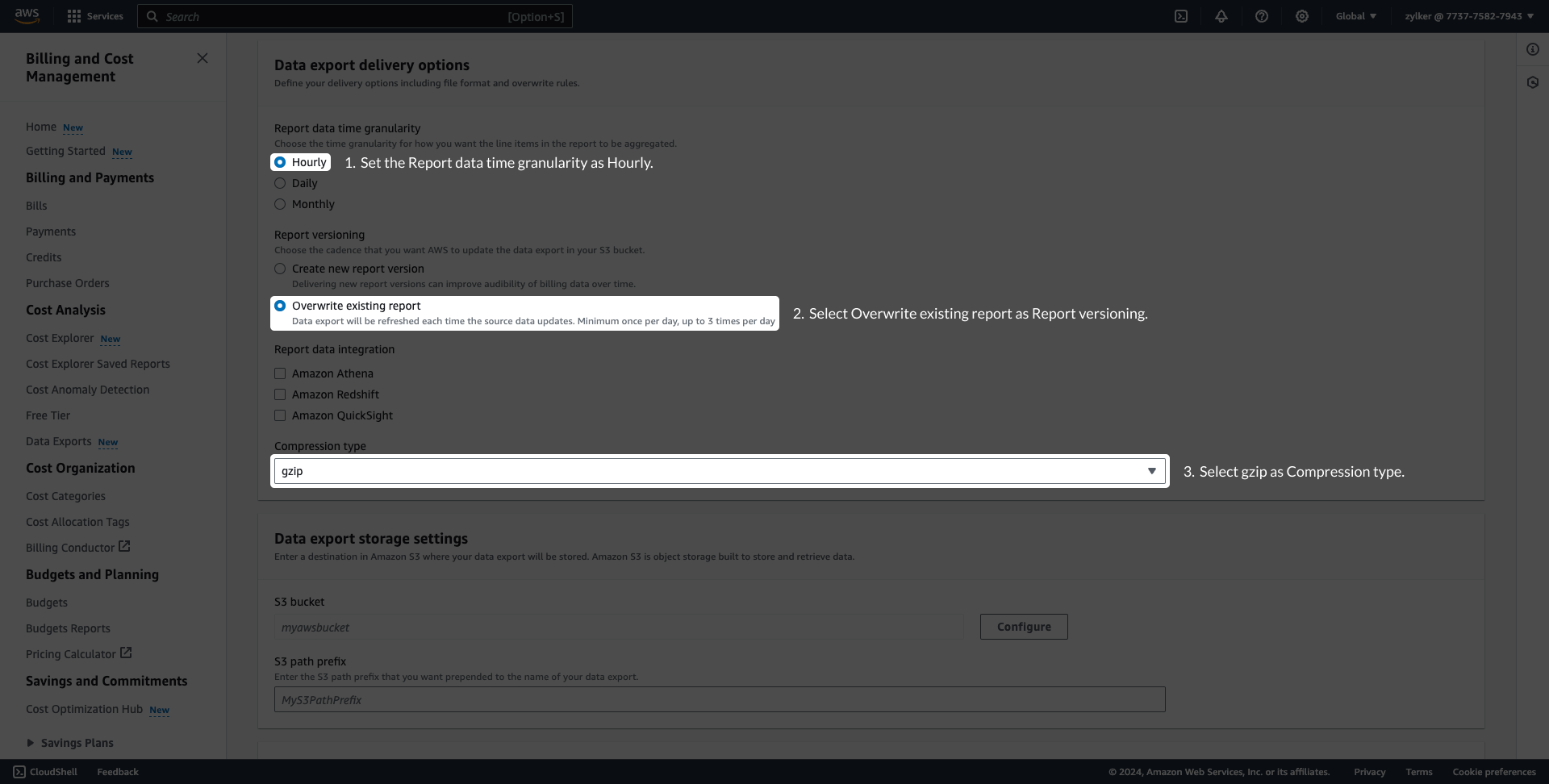
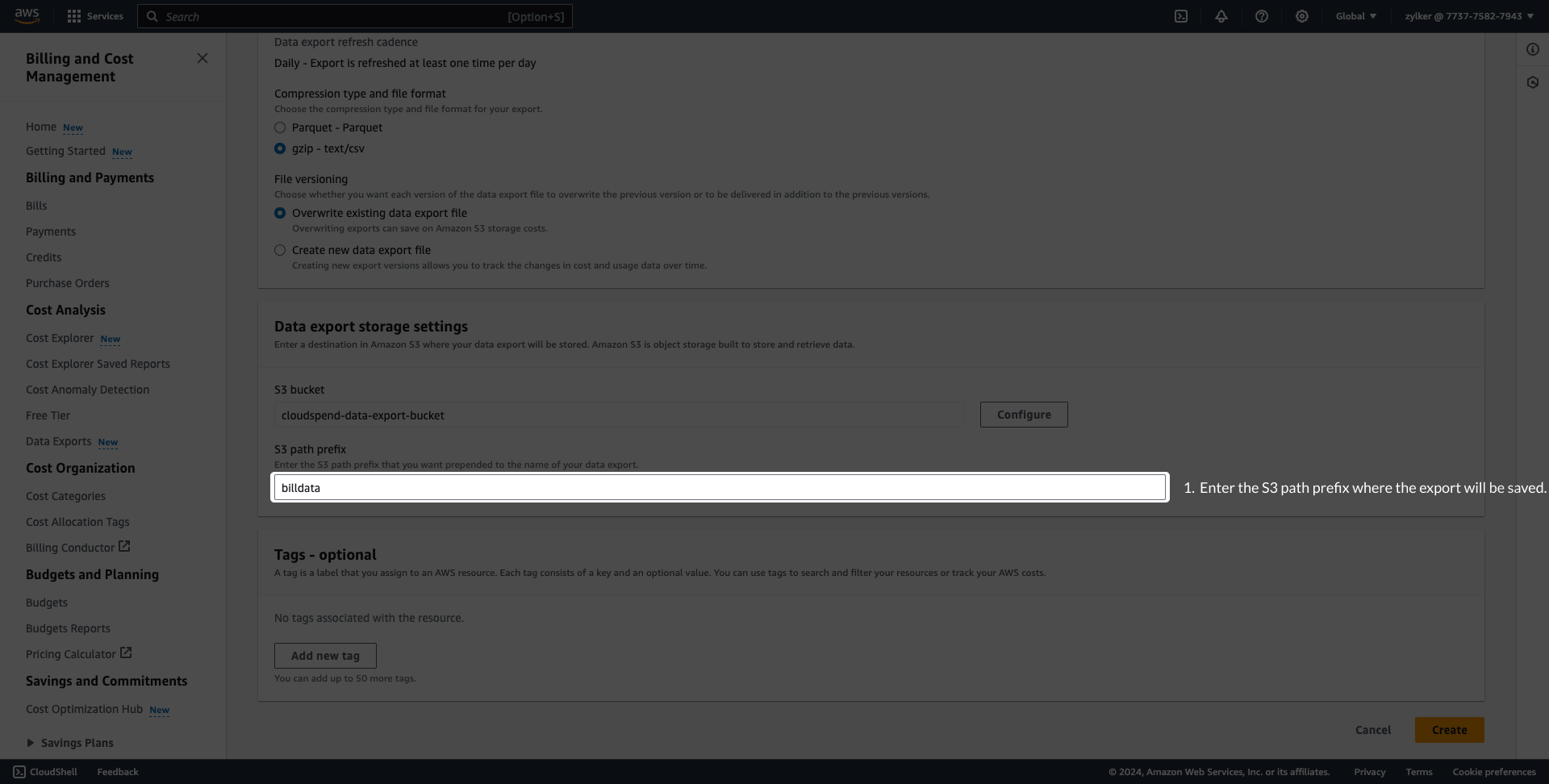
 Configure data exports (Stage 2)AWS Data Exports enables you to create exports of the Cost and Usage Report (CUR) 2.0 or Legacy Cost and Usage Reports. CloudSpend supports master and linked accounts. If you're using the consolidated billing feature in AWS Organizations, then create the data export at master account level. However, if you wish to view the cost and usage details at the linked account level, you have to create the data export for the respective linked account. Exports are delivered on a recurring basis to an Amazon S3 bucket. To deliver the exports to an existing or new S3 bucket, follow the steps mentioned below. If you're already publishing the export to a S3 bucket, skip to Stage 3. Creating a Data exportTo create an AWS data export in an S3 bucket, follow the steps below to get started.
Connect AWS account (Stage 3)Configure the Integrate AWS account page
Connecting a Site24x7 account with CloudSpendConnect your Site24x7 account directly with CloudSpend by:
Connecting a MSP account with CloudSpendConnect your Site24x7 MSP account directly with CloudSpend by:
Support for Linked AccountsYou can now leverage the cloud cost management tool for your linked accounts in AWS by choosing the Account Type as "Linked Account" in the Integrate account page. When you select a linked account, in addition to specifying the report name, specify the S3 bucket name and bucket prefix (if configured) to store the reports. Support for Parquet formatThe CloudSpend AWS cost supports Parquet and GZIP file formats. For cost accounts parsed from the Parquet format report, the user-defined tags with camel case, colon, and hyphen will be replaced with an underscore and follow lower casing. See the below table for examples:
The system-generated tags will not have any changes. Configuration Error AccountsYou can now easily view the errors in configuring your CloudSpend account, like Invalid report name or Expired roles in the Configuration Error Account(s) section. Choose to either edit or delete the configuration error and rectify the errors for all accounts from a single view.
©2024, Zoho Corporation Pvt. Ltd. All Rights Reserved. |
||||||||||
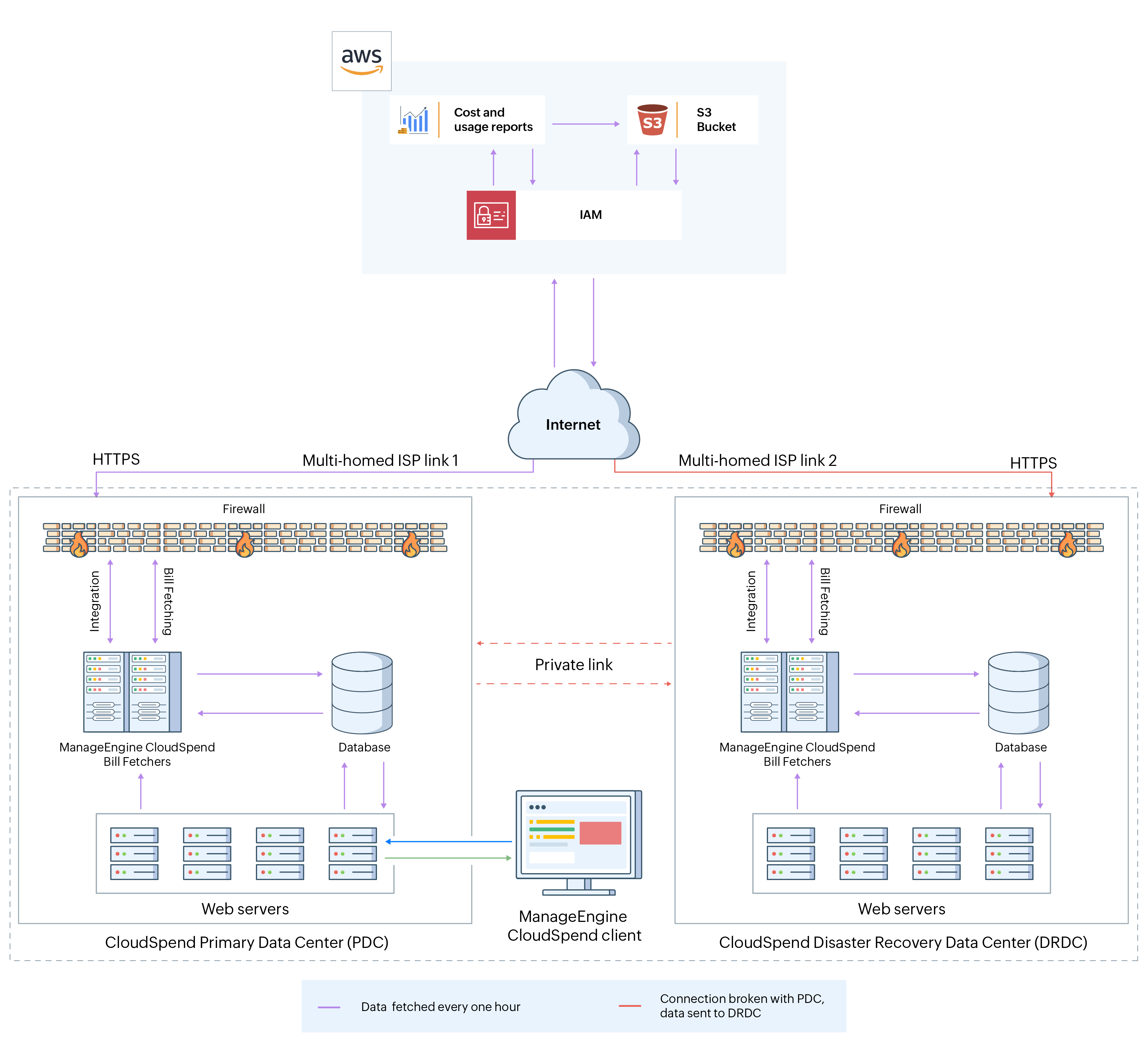 CloudSpend-AWS integration architecture
CloudSpend-AWS integration architecture